How to enter the manual control system security risk from SCADA to ICS, how to solve security risks?
How to avoid the safety hazards of industrial control systems, Siemens SCADA system has caused great panic in domestic industrial enterprises. At present, domestic enterprises are not strong enough to slow down the deployment of SCADA systems. So where should we start to strengthen SCADA? System security protection. From SCADA to ICS, how to solve security risks?
In 2010, Iran’s nuclear facility was hit by the world’s first destructive virus attack specifically for industrial control systems. The worm called Stuxnet was specifically targeted at the Siemens SIMATIC WinCC Monitoring and Data Acquisition (SCADA) system, controlled by tampering centrifuges. The instructions caused the centrifuge to stop running, seriously affecting the progress of Iranian uranium enrichment. Due to the wide application of Siemens SCADA system in China's industrial control field, the emergence of Stuxnet worm has caused great panic among domestic industrial enterprises.
I. Security Risk Analysis of SCADA SystemSCADA is a data acquisition and monitoring system, which is widely used in industrial control systems of power, petroleum, metallurgy, natural gas, railway, water supply, chemical and other important industries to achieve data collection and operation status monitoring of the underlying industrial equipment. Implementation and on-site control provide support. Nowadays, with the deep integration of the two technologies and the continuous advancement of the intelligent manufacturing strategy, SCADA, a system between the office network and the industrial control network, is facing increasingly serious security challenges. Hackers can easily use the office network or the Internet as an entrance. Security vulnerabilities in SCADA systems attack industrial control systems, causing serious security incidents and immeasurable economic losses.
1. The fault of SCADA application configuration of a large domestic wind power enterprise
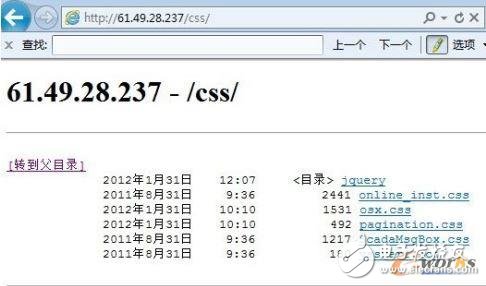
Search the company's SCACA information through the network, the result reveals the IP address of the SCADA system, click on the link http://61.49.28.237/ to open the directory browsing, traverse the directory to get CKFinder, then use the getshell command to control the SCADA host, through the front end The WEB server and the database server act as a springboard, and operate the central control system of the back end through a VPN or the like.
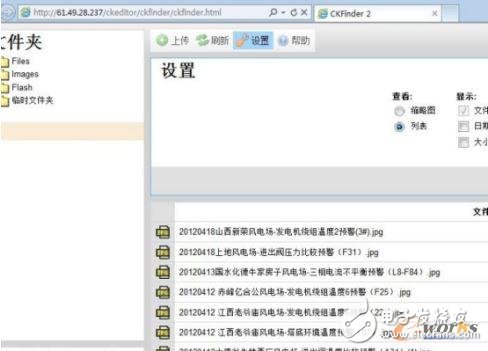
A hacker can find a oracle injection vulnerability in the website through a simple vulnerability scan of the official website of a power system. Through the SQL injection operation, the oracle is injected into the intranet. It is found that although the machine is placed on the intranet, the DMZ area is not separately configured. Using the working group, you can gain access to the domain through permissions. At that time, at least three SCADA hosts were discovered with an infiltrating attitude. At this step, it is not difficult to control the SCADA for the hacker who knows the industrial control system. Realized.
From two cases, we can get a preliminary conclusion. At present, domestic enterprises are not strong enough to slow down the deployment of SCADA systems. Many SCADA attacks can start from the web and use the web as a breakthrough to infiltrate the intranet. To control permissions. For the attacker, basically only the target is determined, because the SCADA system has poor protection ability, the attacker is very easy to get the higher functional authority. With this privilege, it is easy for an attacker to shut down important industrial facilities and cause serious industrial safety incidents.
For some enterprises with higher security levels, in order to avoid the aforementioned security risks, the physical isolation of office networks and industrial networks has been realized in the enterprise. Most of the attacks on such enterprises are attackers of the ferry, which are attacked by acquiring the trust of the enterprise content intermediary. The approximate process is: the first step is to obtain the workflow of the target company and related personnel information. The second step is to obtain the physical location of the target industrial control system and related information of the engineer, including but not limited to family background, work background and other information; the third step is to falsify one's identity, for example, to communicate and form contact and master more Target information; Fourth, after obtaining the target trust, the U disk is used to initiate a ferry attack. The Iranian nuclear plant centrifuge shutdown caused by the earthquake virus is a typical attack by a man-in-the-middle.
Therefore, for the safety of industrial control systems, it is necessary to make up for it, but pre-existing prevention is more important. Enterprises need to do a good job in SCADA system security protection in advance.
Second, the safety hazards of industrial control systemsTalking about the protection of the fragile SCADA system, let's talk about the hidden security risks of the industrial control system itself. Before we do that, let's first understand how the industrial control system differs from the IT system in terms of security architecture.
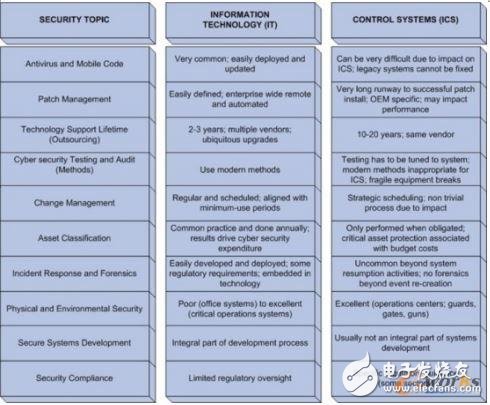
(1) Anti-virus: It is very common in IT systems and is easy to deploy and update. Because industrial control systems are all solidified, deploying anti-virus software is very difficult.
(2) Patch management: Whether the remote or local system is updated regularly in the IT system. In the industrial control system, since they are all dedicated systems, they are worried about affecting performance and basically do not update the patches.
(3) Technical support cycle: IT systems have many suppliers, easy upgrades, and fast technology update cycles, basically 2 to 3 years; industrial control systems are dedicated suppliers, possibly one or several, technical updates The cycle is around 10 to 20 years.
(4) Network security testing and auditing: IT systems use the most modern methods; industrial control systems rarely have security testing and auditing.
(5) Incident response and forensics: IT systems are easy to deploy and easy to obtain evidence; failure of industrial control systems is difficult to obtain evidence in addition to updating the system.
(6) Security system development: IT system integration is in the development process; the industrial control system does not have a common integrated development process.
Maybe you will ask why there are so many risks in the industrial control system but there are not a lot of security problems? This question is well explained. Industrial control systems have been developed for so many years. Due to the use of professional hardware and protocols, and rarely directly connected to external networks or office networks, there are fewer hackers who understand IT technology and understand industrial automation control technology, although industrial control networks Attacks have occurred, but not many.
However, with the integration of IT and OT, the previously closed dedicated industrial network has begun to open up. More and more standardized hardware and software have emerged in industrial control systems, such as commercial PCs and servers based on X86 architecture. Fieldbus technology has been gradually replaced by industrial Ethernet for many years, and the network protocol has changed from a complicated bus protocol to a TCP/IP protocol. From another perspective, with the interconnection of middle and upper management business systems such as ERP, CRM, MES and lower-level PLC, DCS and other production control systems, intelligent terminals and wireless technologies have also been applied in the field of industrial control. Even if the physical security protection of the enterprise is no better, it will not work.
Third, from SCADA to ICS, how to solve security risks?With the development of hardware and software and network technology in the industrial control system in the direction of generalization and standardization, the security system of the industrial control system is being defeated and becomes unprecedentedly fragile. This status quo has also caused concern and attention from the national sector.
In response to the security risks faced by industrial control systems, the Ministry of Industry and Information Technology issued the "Notice on Strengthening Information Security Management of Industrial Control Systems" in September 2011, clarifying the organizational leadership, technical support, rules and regulations, etc. of information security management of industrial control systems. Requirements. On June 28, 2012, the State Council issued the "Several Opinions on Vigorously Promoting the Development of Informatization and Effectively Protecting Information Security." Clearly required to ensure the safety of industrial control systems, focusing on strengthening supervision of industrial control systems that may endanger life and public property. Conduct safety evaluations on key products and implement safety risk and vulnerability notification systems.
Guided by a series of policy documents, industry security vendors are also constantly strengthening the security protection capabilities of their security products for industrial control systems. In recent years, domestic industrial safety manufacturers, including Yan En Network, Wei Nuo, Gu Shen Xing, and Li Huan Huaan, have launched system-based solutions for the safety problems faced by industrial control systems, and achieved good results.
The author believes that as closed industrial control networks begin to open up, more and more standardized hardware and software have emerged in industrial control systems, which is the trend of industrial transformation in the future. As the link between office network and industrial control network, SCADA system is a key part of reducing the security risk of industrial control system. In this regard, we suggest that the security protection of SCADA systems can be strengthened from the following aspects:
1. Evaluate requirements and connect to the SCADA network. Conduct in-depth testing and vulnerability analysis of the remaining connections to the SCADA network to assess the security status of these paths. Use this information and SCADA and risk management procedures to generate a robust protection strategy for all links in the SCADA network. Since the security of a SCADA network depends on its weakest connection point, it is important to use industrial-grade boundary isolation systems, industrial-grade intrusion detection systems, and some other security strategies at each entry point.
2. Consolidate the SCADA network by canceling or reducing some unnecessary services. Operating systems based on commercial or open source can be attacked through many default network services. To minimize, ignore, cancel unused network services or background, to reduce direct network attacks. Unless the risk assessment shows that the benefits of this service far outweigh the risks posed by its potential risks, the SCADA network must not be allowed to use a service or performance.
3. Don't rely on proprietary protocols to protect your system. Some SCADA systems use separate, proprietary protocols to support communication between field devices and servers. Often the security of these SCADA systems is based solely on the confidentiality of these protocols. However, unfortunately, the secret security provided by the confidentiality agreement is less pitiful. So don't think it's safe because it's a proprietary protocol. In addition, suppliers are required to close all backdoors or supplier interfaces on the SCADA system and ask them to provide a system that can be protected.
4. Strictly control all the ways to be the back door of the SCADA network. If there is a backdoor or vendor connection on the SCADA network, verification is strictly performed to ensure secure communication. Wireless and wired networks for modem, communication, and maintenance are the most vulnerable parts of SCADA networks and remote sites.
5, the implementation of internal monitoring audit, external intrusion detection, to ensure 24 hours a day monitoring. In order to respond effectively to cyber attacks, a monitoring strategy is used to alert network administrators when malicious behavior is caused by resources from the Internet or external sources. The detection system works continuously for 24 hours and this function can be easily set. In addition, the incident response procedure must be appropriate to make an effective action when an attack occurs. In order to perform the monitoring function of the network, the log function is enhanced on all systems, and the log is audited every day to detect suspicious behavior in real time.
6. Conduct physical security surveys and evaluate remote sites connected to the SCADA network to evaluate their security. Any part that is connected to the SCADA network is the target to be inspected and evaluated, especially the unmanned station. On each device, a physical security check is performed. Identify and evaluate all information resources, including telephone and computer networks, fiber optic cables that may be eavesdropped; radio and microwave lines that may be utilized; computer terminals that may be accessed; access points to wireless networks. Eliminate simple point failures. The security of these points is sufficient to prevent unauthorized access, and it is not allowed to set up active access points on remote or unprotected sites for convenience only.
In-ear earphones are sometimes referred to as earbuds, and they refer to earphoees that are small enough to fit into the ear. The Sport Earphone are written with L and R, L is left for the left channel, and R is the right for the right channel. In principle, the thinner the earmuffs, the more comfortable they are. However, the thin earmuffs will be less soundproof.
Correct use:
1: Set the volume of the source to the minimum.
2: Insert the 3.5mm plug of the in-ear earphone into the earphone jack.
3: Adjust the volume to a position that sounds comfortable. In-ear earphones are not recommended for driving motorcycles, bicycles, operating machines, and jogging, as you may affect your judgment of potential hazards.
4: Do not open the volume too much during use.
5: When pulling the earphone plug, you should pinch the hard plastic part of the back end of the plug and pull it out, instead of pulling it straight out through the wire.
6: Avoid excessive bending of the wire for a long time.

In Ear Headphones,Sport Earphone,In Ear Earphones,Zipper In Ear Headphones
Shenzhen Linx Technology Co., Ltd. , https://www.linxheadphone.com