With the rapid development of IoT communication technology, the rise of Low Power Wide Area (LPWA) technology has emerged. LPWA technology is mainly for low-power, wide-coverage, long-distance, low-bandwidth IoT services, and its representative technologies include LoRa (Long Rang, LoRa), Sigfox and license-based based on unlicensed spectrum. Narrow Band Internet of Things (NB-IoT) [1-3].
NB-IoT is an LPWA cellular solution developed by 3GPP (3GPP) to support cellular systems introduced in ultra-low complexity and low-throughput Internet of Things. It has low cost, low power consumption, large connection and wide range. Coverage and other advantages [4-8]. As an emerging wireless access technology in cellular systems, NB-IoT meets the requirements of delay-insensitive, minimum-rate requirements, large transmission interval, and low transmission frequency. The key technical processes of the sub-layer and each sub-layer are simplified accordingly, and the random access process for implementing the initial access network and uplink synchronization of the User Equipment (UE) is also included [9-10 ]. In the NB-IoT system, the purpose of using random access is similar to that of LTE, and is also used to implement initial access and uplink synchronization when the UE establishes a wireless link. However, due to the business requirements of the NB-IoT technology, the frequency of initiation of the random access procedure is very low. Therefore, it is necessary to design an access process solution for NB-IoT to support its business needs.
1 Application scenario of the random access process
In NB-IoT, similar to LTE, the UE also performs random access procedures in idle mode and connected mode, but NB-IoT only supports contention-based random access and arrives in downlink data in R13 (Release 13). Random access triggered by PDCCH order in case. In addition, it does not support the PUCCH channel and the handover function. Therefore, the related application scenarios for triggering random access in the NB-IoT system are also simplified into the following four types [12-13]: (1) Radio resource control ( Radio Resource Control (RRC) initial access procedure in idle state; (2) RRC connection reestablishment process; (3) RRC connection state, when receiving downlink data (uplink out-of-synchronization); (4) RRC connection state, sending When the data is uplinked (when the uplink is out of synchronization or when a scheduling request is triggered).
In the above application scenario, only the first scenario is a random access process in the idle mode, and the remaining three scenarios are random access processes in the connected mode, and the random accesses triggered by the four scenarios are all It is a competitive based approach.
2 four steps of the random access process
The contention-based random access procedure in NB-IoT is similar to LTE, which is still composed of 4 steps [14-15]: (1) the UE sends a random access preamble (message 1); (2) the UE receives the network to send Random access response (message 2); (3) UE sends Msg3 (message 3); (4) contention resolution (message 4). However, in order to support the characteristics of NB-IoT, each step of random access is optimized accordingly. The following is a detailed analysis of each step of the NB-IoT optimized random access procedure.
2.1 Random access PRACH resources and preamble selection and transmission
In the NB-IoT system, the UE needs to determine the PRACH resource before sending the random access preamble. The selection of PRACH resources can be divided into two types: one is a PRACH resource explicitly indicated by a base station (eNB); and the other is a PRACH resource selected by the UE. The PRACH resource selected by the UE is different from the LTE. The NB-IoT UE selects the PRACH resource according to its corresponding coverage level. The NB-IoT defines a total of three coverage levels, namely level 0, level 1, and level. 2, and each coverage level is provided with a corresponding PRACH resource configuration parameter, wherein the configuration parameter is sent to the UE through the SIB2-NB in ​​the system information block, and is provided in the nprach-ParametersList, mainly including [16]: PRACH repetition Number of times (determined by the parameter numRepetitionsPerPreambleAttempt), PRACH time domain resources (including period: nprach-Periodicity, starting subframe position: nprach-StartTime, etc.) and PRACH frequency domain resources (including subcarrier offset: nprach-SubcarrierOffset, sub The number of carriers: nprach-NumSubcarriers and other parameters) and two parameters for preamble repeated transmission, namely: the maximum number of preambles (maxNumPreambleAttemptCE), the maximum number of attempts per preamble (numRepetitionsPerPreamblePreambleAttempt), and the UE is at the same time The coverage level is based on downlink measurements (eg, Reference Signal Received Power (RSRP)) and its threshold parameters. Judging by number.
After the PRACH resource is determined, the selection of the random access preamble is performed, and the selection of the preamble is the same as the determination of the PRACH resource, and can also be divided into an eNB explicit indication and a UE selection. The eNB explicitly indicates that the preamble is different from LTE. Since NB-IoT does not support random access in non-contention mode in R13, only the random access triggered by PDCCH order will be explicitly indicated in the case of scenario 3 mentioned above. Leading. If the preamble is indicated by the eNB, the UE sets the preamble according to the PDCCH order carrying the subcarrier number (ra-PreambleIndex) specified by the base station and the PRACH resource specified by the base station of the current coverage level. That is, the preamble is set to nprach-SubcarrierOffset+(ra-PreambleIndex modulo nprach-NumSubcarriers), where nprach-SubcarrierOffset and nprach-NumSubcarriers are parameters of the PRACH resource specified by the base station of the current coverage level. The preamble selected by the UE is also different from LTE. The random access preamble sequence in NB-IoT will not be divided into group A and group B, and does not need to be generated by Zadoff-Chu sequence, but consists of 5 symbols. And there are 4 Symbol Groups consisting of 5 symbols, and all the sequences of the symbol groups are configured by default all 1s. Therefore, when selecting the preamble, select the symbol group first, then select the preamble in the symbol group, and select The preamble will all be a sequence symbol for 1. The specific process of random access resource selection is shown in Figure 1.
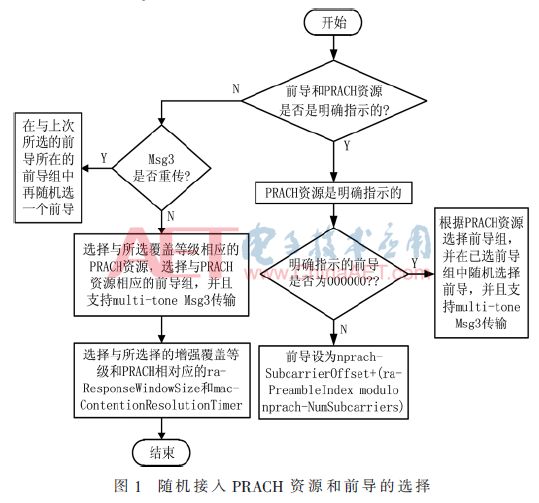
The selection process of the random access PRACH resource and the preamble shown in FIG. 1 is different from that of LTE. The Multi-tone shown in the figure is a transmission mode of the transmission Msg3 (message 3) in the random process, in the NB- In the uplink of IoT, it can be divided into two transmission modes: Single-tone and Multi-tone. However, in early NB-IoT field trials and deployments, some UE implementations may not support Multi-tone, but before scheduling uplink transmissions, the eNB should know if the NB-IoT UE supports Multi-tone transmission. Therefore, the UE should inform the eNB in ​​its random access message 1 by transmitting the subcarrier index occupied by the preamble to indicate its support for Multi-tone in order to facilitate the scheduling of the uplink transmission by the network in Msg3. To this end, a parameter is introduced in the frequency domain resource of the PRACH resource: nprach-SubcarrierMSG3-RangeStart, whose parameters take values ​​of 0, 1/3, 2/3, 1, and pass the formula: nprach-Subcarrier-Offset+(nprach- The result calculated by SubcarrierMSG3-RangeStart·nprachNum-Subcarriers) may divide the NPRACH subcarriers in the frequency domain into two non-overlapping sets, and the UE may select one of the two sets to transmit its random access preamble. However, in R13 NB-IoT, the UE usually uses the Single-tone method to transmit the preamble. In other words, the value of the nprach-SubcarrierMSG3-RangeStart parameter is always 1, indicating that Multi-tone is not supported when Msg3 is transmitted.
After the NB-IoT UE selects the PRACH resource and the preamble, the target preamble transmission power (PREAMBLE_RECEIVED_TARGET_POWER) needs to be set, and its setting is also different from LTE. First, based on the formula for calculating the target preamble transmission power of LTE, the value of the target preamble transmission power of the LET is obtained. For the NB-IoT UE, the value of DELTA_PREAMBLE is 0 in the formula; and then according to the coverage level of the UE. It is set that when the coverage level is 0, the target preamble transmission power is set to: PREAMBLE_RECEIVED_TARGET_POWER-10*log10 (numRepetitionPerPreambleAtte-mpt), and when the coverage level is 1 and 2, PREAMBLE_RECEIVED_TARGET_POWER is set to the corresponding maximum UE output power. After the PREAMBLE_RECEIVED_TARGET_POWER is set, the selected PRACH resource corresponding to the selected coverage level, the corresponding RA-RATI, the preamble index or the NB-IoT subcarrier index, and the PREAMBLE_RECEIVED_TARGET_POWER are used to transmit the preamble transmission corresponding to the selected preamble group. The predecessor of the number of repetitions.
2.2 Random access response
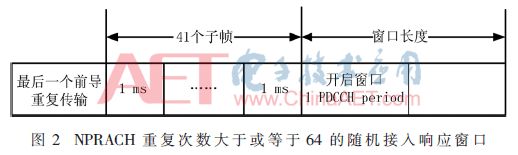
Similarly, in NB-IoT, once the random access preamble is sent out, the Media Access Control (MAC) entity in the UE will be turned on for receiving random access regardless of whether the measurement gap is likely to occur. The PDCCH for the RAR identified by the random access radio network temporary identifier (RA-RNTI) defined by the formula (1) is monitored in the RAR window of the response (Random Access Response, RAR). Due to the specific uplink transmission scheme in NB-IoT, in order to support the repeated transmission characteristics, the location of the RAR window is different from that of LTE, and it is related to the number of repetitions of NPRACH, which is divided into two cases:
(1) When the number of NPRACH repetitions is greater than or equal to 64, the RAR window shall be opened with 41 subframes at the end of the last preamble repeated transmission, as shown in FIG.
(2) When the number of NPRACH repetitions is less than 64, the RAR window at this time should be opened with 4 subframes at the end of the last preamble repeated transmission, as shown in FIG.
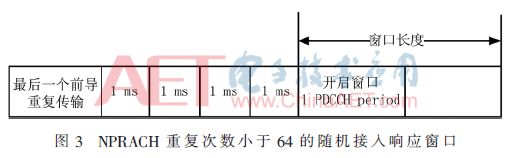
In NB-IoT, the RAR window lengths in FIG. 2 and FIG. 3 are also extended. Instead of using the 10 ms RAR window in LTE, the PDCCH period (PP) is used as the RAR window. The unit of length, the value of which is unchanged, the same as the minimum RAR window is defined as 2 (this article sets the window to 2 PP), the maximum is 10. At the same time, RA-RNTI is newly defined, and its formula is defined as follows:
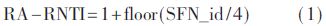
Where SFN_id is the index of the first radio frame of the designated PRACH, which also corresponds to the index of the first radio frame transmitted by the preamble. In NB-IoT, the composition parameters of the MAC PDU received by the random access response are the same as those of LTE, but it should be pointed out that the NB-IoT UE has a backoff identifier (BI) in the composition parameters of the PDU in order to meet its service needs. The corresponding backoff parameter value has been greatly increased, and the maximum value of the parameter value is 524 288 ms, which is the delay time for repeatedly transmitting the preamble. At the same time, since the UEs use the same preamble, and each subcarrier of the random access preamble group corresponds to one random access preamble, the random access preamble identifier (RAPID) used to determine whether the random access is successful only needs to correspond to the preamble. The subcarrier index is started. When the RAPID is consistent with the starting subcarrier index, the random access response is considered to be successfully received, and the monitoring of the PDCCH is stopped. The receiving process of the random access response is shown in FIG. 4.
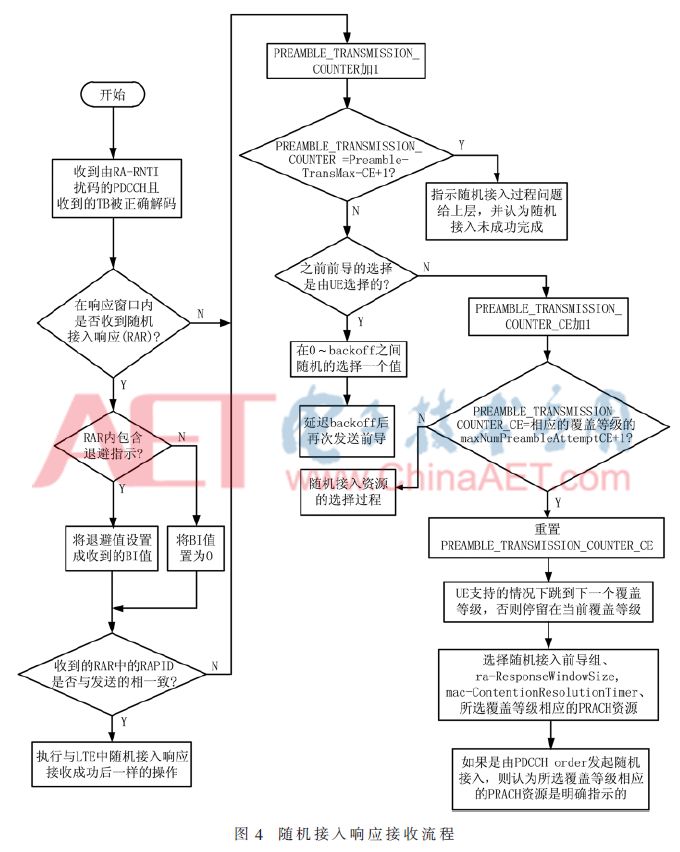
As shown in FIG. 4, when the received RAPID is inconsistent with the transmission or the RAR is not received in the RAR window, the UE will perform preamble repeated transmission, but in the NB-IoT, since the UE has three coverage levels, Therefore, the preamble repeat transmission counter corresponding to each coverage level introduces a new parameter, namely: PREAMBLE_TRANSMISSIN_COUNTER_CE, and the UE still does not receive the RAR after the lower coverage level reaches the maximum number of times it allows the preamble to be transmitted. When the received RAPID is inconsistent with the transmission, the UE will skip to the next higher coverage level, and then judge the corresponding counter according to the maximum number of preambles allowed to be sent according to the current coverage level. If the current coverage level is the highest coverage level, then stay at the current coverage level and retry the preamble transmission from the PRACH resource. At the same time, the parameter PREAMBLE_TRANSMISSION_COUNTER used for counting in LTE will be used as a total counter to determine whether the random access procedure in NB-IoT is successful. When it reaches the maximum value, the NB-IoT UE directly considers that the random access is not successfully completed. .
2.3 Message 3 transmission
In NB-IoT, Msg3 is also used for RRC connection setup request, but in order to reduce the signaling overhead of handover between UE and eNB in ​​idle state and connection state, a Suspend-Resume procedure and a new RRC state are added [ 17], ie RRC-SUSPENDED. When the UE performs data transmission in the RRC-SUSPENDED state, it needs to send the Resume ID for entering the connection state to the eNB through the Msg3 in the random access procedure. Therefore, Msg3 in NB-IoT needs to have enough space to accommodate the 40-bit Resume ID, and the Msg3 transport block size is extended to 88 bits. At the same time, since the control plane optimization scheme for transmitting a small amount of data is newly added in the NB-IoT, in this optimization scheme, after the random access competition is solved, the UE can directly transmit the service data on the message 5, so a new one is added. The data volume and power headroom report is reported to the eNB in ​​the form of a MAC control element in Msg3, so that the eNB can reasonably allocate resources to the UE.
2.4 Competitive solution
In NB-IoT, the competition solution is the same as LTE. It is also a process to solve the conflict problem. The implementation process of the two is basically the same. The difference is that after the NB-IoT UE sends the Msg3, the contention resolution timer needs to be enabled. The contention resolution timer is similar to the RAR window. It does not use the subframe as the length unit, but adopts the PDCCH period. As its length unit. At the same time, its value has also been adjusted accordingly. The minimum defined length is 1 PP, and the maximum is defined as 64 PP. If the contention resolution timer does not time out, and the C-RNTI MAC control element is included in Msg3, the random access procedure is considered to be successfully completed, but it is worth noting that in order to utilize its radio resources more efficiently on the anchor carrier In NB-IoT, it is necessary to first determine whether a non-anchor carrier is provided. Therefore, when a non-anchor carrier is provided, the uplink grant and downlink assignment included in the PDCCH on the anchor carrier are only valid for the non-anchor carrier. If the contention resolution is unsuccessful and the PREAMBLE_TRANSMISSION_COUNTER global counter reaches the maximum value, then the random access is not considered successful in the NB-IoT.
3 random access process test and result analysis
Protocol testing can be implemented in a variety of ways. The TTCN-3 test language is widely used in standard validity verification and protocol conformance testing. It is a standardized test language that can be applied to a variety of test scenarios. In this paper, a TTCN-3-based conformance test platform is built for the random access process of NB-IoT, and its consistency test is performed. At the same time, its simulation diagram is generated, as shown in Figure 5.
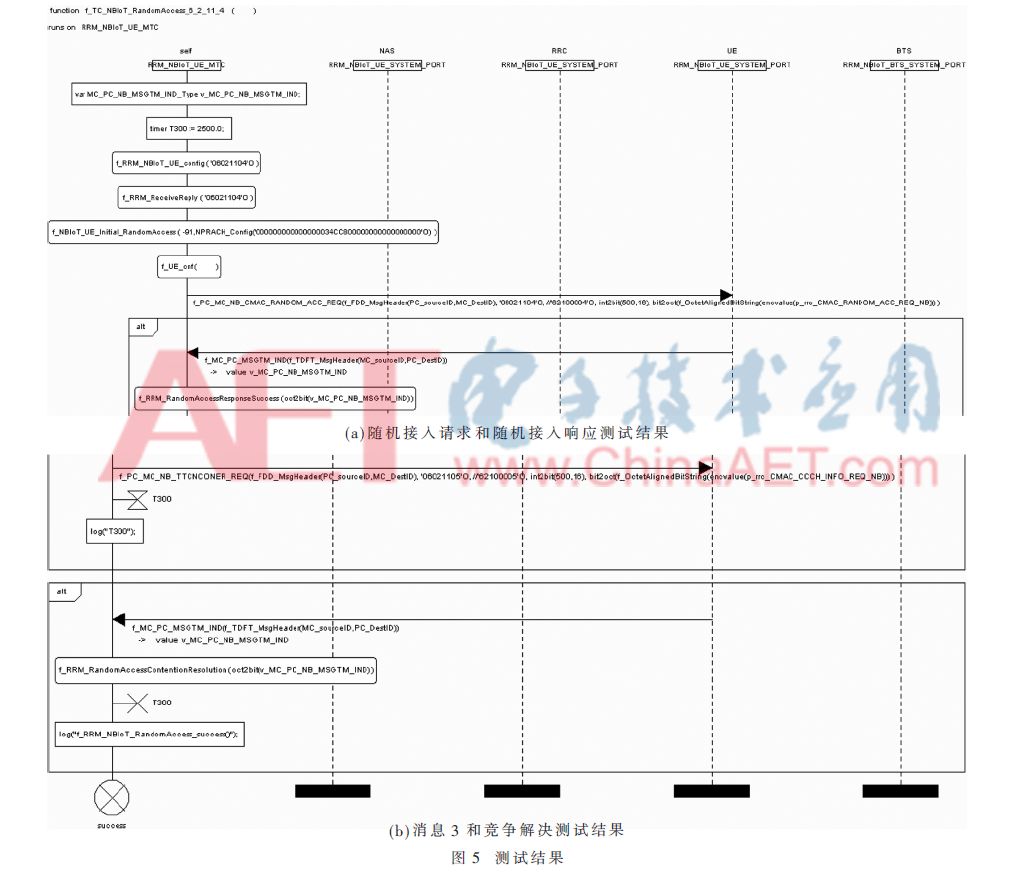
This test is based on the NB-IoT random access conformance test procedure specified in the standard. Finally, the result of the random access process test is judged by the output of the main control log analysis module of the TTCN-3 platform. First, it is judged whether the NB-IoT UE and the base station can communicate normally by the results of the functions f_RRM_NBIoT_UE_config ('06021104'O) and f_RRM_ReceiveReply('-06021104'O) in FIG. 5(a). After verifying the communication, the NB-IoT UE is initialized by the f_NBIoT_UE_Initial_RandomAccess() function to ensure that it enters the state 2A-NB, and the corresponding coverage level configuration is performed according to the RSRP, and the NPRACH resource is configured according to the configured coverage level, and then according to The four steps of random access were verified. At the same time, it is judged whether the random access response and the contention resolution are successful, and whether the success is successful by the functions f_R-RM_RandomAccessResponseSuccess() in FIG. 5(a) and the success and failure of the log output in the function f_RRM_RandomAccessContentionResolution() in FIG. 5(b) respectively; After the random access response is successfully received, the timer T300 is enabled according to the T300 output of the log. The timer value is 2 500 ms. After the NB-IoT UE initiates the Msg3, the T300 is started, as shown in Figure 5(b). Shown. If the contention resolution is received when the T300 has not timed out, the timer is closed, and the f_RRM_NBIoT_RandomAccess_sucess() is output in the master log, indicating that the random access procedure is successfully completed, and then the NB-IoT UE enters the connection state, and the test result is obtained. Meet the consistency requirements of the protocol test.
4 Conclusion
This paper briefly introduces the NB-IoT based on the licensed spectrum, considering the importance of random access for the initial access and uplink synchronization of the UE and its corresponding optimization in NB-IoT, and currently in the middle NB of R13 IoT only supports the random access process based on the competition mode. Therefore, the four steps of the optimized competitive mode-based random access process are analyzed in detail, and a TTCN-3-based conformance test platform is built. And conducted a conformance test.
Copper Tube Terminals Without Checking Hole
Our company specializes in the production and sales of all kinds of terminals, copper terminals, nose wire ears, cold pressed terminals, copper joints, but also according to customer requirements for customization and production, our raw materials are produced and sold by ourselves, we have their own raw materials processing plant, high purity T2 copper, quality and quantity, come to me to order it!
Copper Tube Terminals Without Checking Hole,Cable Lugs Insulating Crimp Terminal,Cable Connector Tinned Copper Ring Terminal,Tubular Cable Lugs Crimp Terminal
Taixing Longyi Terminals Co.,Ltd. , https://www.lycopperlugs.com