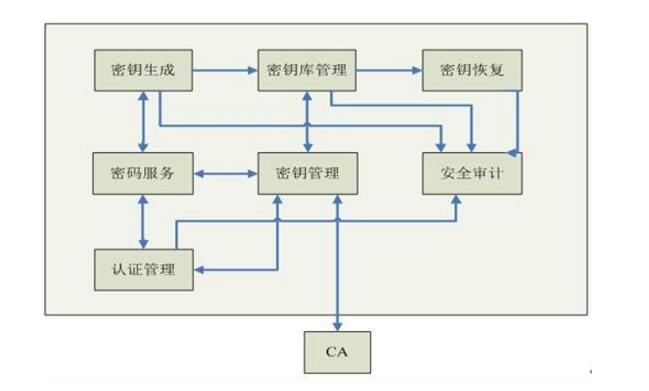
The key, that is, the key, generally refers to various encryption technologies applied in production and life, and can effectively supervise personal data and enterprise secrets. Key management refers to the behavior of managing keys, such as encryption. Decrypt, crack, etc.
Key management includes everything from the generation of keys to the destruction of keys. Mainly manifested in the management system, management protocols and the generation, distribution, replacement and injection of keys. For military computer network systems, due to the user's mobility, affiliation and coordinated operational command are complex, so higher requirements are placed on key management.
a) Basic key or initial key: The basic key is a key selected by the user and allocated by the system to the user, which may be dedicated to the user for a long time, also called a user key. The base key and the session key together initiate and control a key generator consisting of an algorithm that sequentially generates a key stream for encrypting the data
b) Session key: The session key is the key used by two communication terminal users to exchange data at a time. When it is used to protect the transmission key, it is called the data encryption key. When it is used to protect files, it is called Is the file key. The session key can be mutually agreed by the communication parties, or can be dynamically given to the communication parties by the system, so it is also called a private key.
c) Key encryption key, which is the key used to encrypt the session or file key transmitted in the communication. Each node in the communication network has such a key.
d) Host Master Key: The host master key is a key that encrypts the key encryption key and is stored in the host processor.
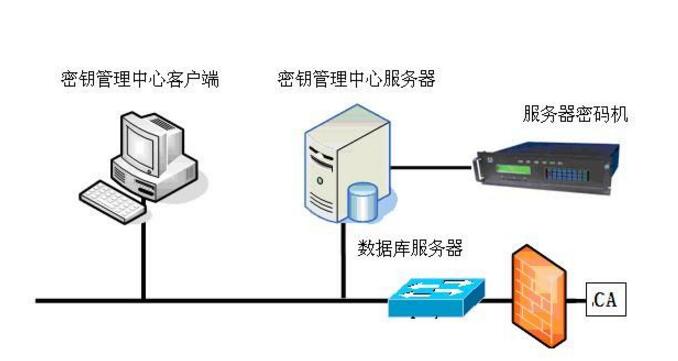
Standardize the confidentiality requirements for the use of keys in the company's product development and production processes to prevent information leakage due to improper operations.
Scope of application:This regulation applies to the management of key use in the company's product design and development and production processes.
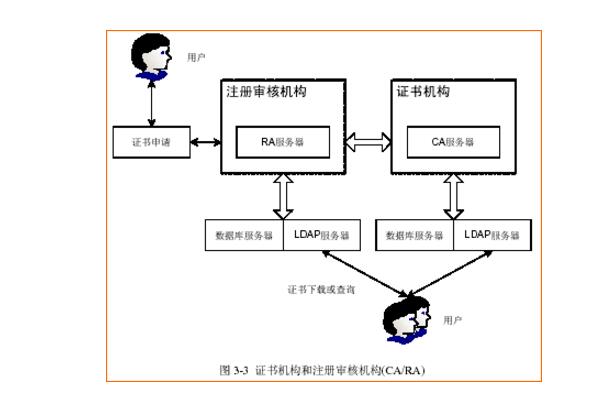
Before you start personalizing, you must create the appropriate encryption key, which must be done as specified in this section. At least the following keys should be generated:
a) Issuer Master Key (KMC): used to derive three keys KMAC, KENC and KDEK.
◠KMAC - used to lock the application area of ​​China's financial integrated circuit (IC) card, and test the personalized data loaded into the card during the personalization process to verify that they are intact and have not been modified;
â— KENC - used to generate IC card ciphertext and verify host ciphertext;
KDEK - used to encrypt confidential data written to the card during the personalization process.
KMC is unique to each issuer, while KMAC, KENC and KDEK are unique to each card.
b) Master Key (MDK) - used to export: UDK - for online card authentication and issuer authentication.
For each BIN (bank identification code), MDK is usually unique, and UDK must be unique for each card. c) The issuing bank's public-private key pair - usually generated by the issuing bank, and the public key should be transmitted to the China Financial Integrated Circuit (IC) card certification body for the creation of the issuing bank's public key certificate. The private key is stored in the issuer's HSM (Host Encryption Module).
d) Key Exchange Key (KEK) - used to encrypt confidential data in the issuer's personalized input file. The KEK of each issuer must be unique.
e) Transport Key (TK) - used to encrypt confidential data in the personalization input file of the issuer that the data preparation system transmits to the personalization system.
Alternatively, these keys can be generated using the issuer's public-private key pair.
f) ICC public-private key pair - The IC card uses this pair of keys to perform DDA and CDA/AC ciphertext generation algorithms. The public key must be signed by the issuing bank's private key to obtain the issuing bank's public key certificate. The ICC public-private key pair for each card must be unique.
g) MDKENC - used to export: UDKENC - used to encrypt the script confidential information of the issuing bank.
h) MDKMAC - used to verify the script information of the issuing bank.
2. Formation and distribution of keysDifferent types of encryption algorithms support different functions in the EMV Card Personalization Specification: 2003. However, when the encryption algorithm is not implemented correctly, the intended role of the encryption algorithm will be negatively affected. A secure implementation will depend on how well different keys required by the specification are managed by the issuer. The purpose of the following materials is to provide an overview of the cryptographic roles played by different algorithm types and the basic requirements necessary to securely manage keys. a) The security of the asymmetric (SM2/RSA) key management IC card depends on the protection of the private key (signature). There is no guarantee that the security of the private key used to sign static or dynamic data elements will expose the IC card to the risk of being forged. The main risks faced by the private key include: - successfully solving the ECDLP problem, and successfully decomposing the RSA modulus; - the leakage of the private key itself.
To limit potential leaks represented by these risks, we recommend the following issuer requirements. The security of the private key (signature) depends on many factors, including:
- the length of the SM2/RSA key modulus bits, for example: 256 or 1024 and 1152; - the quality of the main digits that make up the public/private key modulus;
- methods used to physically protect (protect) private keys (signatures) from unauthorized access and exposure/hazard, especially when IC cards or other secure encryption devices (SCDs) use them. The protection provided by the key.
SM2/RSA Key Generation When generating an SM2/RSA public-private key pair, it is recommended to complete this process in the protected memory of a physically secure device. Such devices must include a random or pseudo-random number generator that performs the original check routine and supports tamper response mechanisms.
- the SM2/RSA private key (signature) may be temporary for physical security equipment;
- Key generation will utilize a random or pseudo-random process to make it impossible to predict any key or to determine that certain keys in the key space are more likely than any other key;
- A personal computer or other similar unsecured device, ie an untrusted device, will never be used to generate an SM2/RAS public-private key pair.
Key Transfer and Storage To protect the integrity of public and private key pairs, it is important for the issuer to ensure that such key data uses the following steps:
- Public keys should be secure and transported in a way that guarantees their integrity. The recommended public key is always transmitted in a data structure such as a certificate, or it can be guaranteed with a message authentication code (MAC), which is a key used only for that purpose in accordance with ISO 9807. The defined algorithm is applied to the public key and related data. It is also recommended to use dual control techniques to ensure that the recipient of the public key has a way to verify its sender and integrity, ie by a separate and independent transmission of a check value on the public key;
- Private keys must be secured and transmitted in a way that guarantees their integrity and privacy. The transport mechanism may include:
a secure encryption device;
The private key of the protected key is decrypted using a symmetric algorithm that is at least equal to the strength of the encryption; as a part (safety on the IC card), and a symmetric algorithm is used for decryption.
Symmetric Key Management The symmetric key in JR/T0025 is used for special transaction functions. The symmetric key is derived from a master derived key (MasterDerivationKey) during personalization. The final card level key is unique. The issuing bank master key includes:
- Issuer Master Export Key (IDKAC): used to derive a card key, which is used to generate a MAC called Application Ciphertext (AC);
- Issuer Security Message Master Key (IMKSMCIMKSMI): used to export card keys, which are used in secure messages between the card and the authentication system, ie card lock, application lock/unlock, update card Specific data and modify PIN.
The key generation issuer will use the following principles to minimize the chance of key data leaking during creation:
- When generating keys, they must either be generated in a physically secure device protected by a tamper response mechanism or must be generated by an authorized staff member as part of it (see below). The device must contain a random or pseudo-random number generator;
- An unprotected key cannot exist outside of the protected memory of a physically secure device at any time. A device that is physically secure at any time cannot output a plain text key unless it is output as a password or in two or more parts;
- When the key is generated by an authorized worker through a process of combining the parts, each party must be required to generate a portion that is as long as the key to be generated. The key combination process takes place inside a physically secure device. In addition, the method of combining the parts should be that it is known that any subset of the parts cannot know the key value. Separate keys are controlled by a regulatory agency, and at least one of the partial holders is an employee of the issuing bank;
- the check digit should be calculated for all of the actual keys;
- Personal computers or similar unsafe devices can never be used to generate keying material;
- If any key is found to exist outside of a physically secure device, or if parts of the key are known or suspected by a single person, then the key will be considered to have been compromised and must be used Replace it with a new key. Key transfer and storage symmetric keys may need to be transmitted and stored. This includes, for example, transferring a symmetric key from the issuing bank's site to a third party processor or card personalization provider. The following measures limit the potential danger of data leakage when a symmetric key is being transmitted or stored:
- symmetric keys can be safely transferred to a security token or smart card for transmission and storage;
- Symmetric keys can only be transmitted or stored within the protected token of a security token or smart card in the following manner:
Using the principle of dual control and separation of secrets, two or more parts are used as passwords, and passwords are created with a transmission or storage key that is securely established by the parties.
3, the preservation of the root key plaintext dataThe root key plaintext data is saved as follows:
a) Once the key information is received, the responsible key manager must immediately check if the parcel has been tampered with and must verify the content;
b) If the receiving manager has any uncertainty about the integrity of the key data, the sender must be notified immediately. The sender and the receiver negotiate to determine the future status of the key data. The basis for any decision to continue to use the key material must be recorded and retained by both parties;
c) If the hard copy data is to be kept for any period of time, each hard copy component, security token or smart card must be stored in a serialized secure envelope;
d) This serialized confidential envelope must be kept in a physically secure container that can only be accessed by a designated key manager or reserver. Each access to key data must be logged, including time, date, envelope serial number, destination, and signature. These logs will be available to any appropriate requesting agency;
e) Key material can never remain outside of the secure envelope and their physical security environment beyond the time necessary to access the task.
4. Save other key dataHere are some general guidelines for key storage issues that apply to asymmetric and symmetric key storage:
a) use of PC board
A PC board that provides encryption services to the host can be seen as a form of HSM and a similar desired level of protection.
Note: The primary reason for using an encrypted security device is to protect the key. If the system using the HSM host is not secure by itself, then the attacker will be more vulnerable to the software functionality of the system, ignoring the HSM.
b) access control
All keys stored outside the card and outside the HSM should be kept under at least dual control. c) HSM and IC secure memory
In general, the HSM will contain separate storage and processing devices, and the key material will be transferred across the internal hardware bus. For this reason, it is important that HSM clears (or zeros) its memory when a hazard is detected. In addition, HSM's hardware design is also important to address electromagnetic radiation issues. HSM is generally designed to be in a safe environment.
5, personnel managementThe person responsible for managing the encryption key and key elements and other key data devices must be assigned by the technical vice president. When assigning someone to monitor key data, sufficient confidentiality controls must be implemented to ensure that no individual or unrecognized individual has any opportunity to read the data component of the key. The key custodian must be an officially entrusted employee and must never be a temporary helper or consultant. In addition, in order to ensure the continuity of the service, the candidate can be regarded as a "backup" of the primary key custodian. The criteria for selecting a "backup" manager should be the same as the criteria for selecting a primary key custodian. Key responsibilities are significant and are an essential part of the issuer's security protocol. The key data they manage is the most important cryptographic opcode in the issuer's card issuer. Each card issuer shall verify the role of the internal key management process and the persons involved in the following operations:
a) The responsibilities of the key management personnel include the control, verification and secure storage of the password data;
b) The responsibility of the key manager or its “backup†is:
â— Receive and securely store key elements;
â— Manage records or logs that read and use key data, including read times, dates, destinations, and re-secure storage;
â— Verify key data transmitted to all designated personnel other than the control authority of the issuing bank;
Sign the destruction of the expired key element to testify;
â— Enter the key data into the security encryption module as often as needed;
â— Guide and monitor the destruction of expired password data based on the notification of the data owner.
c) The key manager at the time of initial generation of the key data shall be responsible for protecting the data and forwarding it to the designated key manager of the receiving unit. This responsibility also includes verification of the data receipt.
The Smart board For Teaching is a teaching device specially designed for educational activities. smart board has all the functions required for the teaching activity scene, such as whiteboard writing, screen sharing, annotation, video playback, teaching tools, VR laboratory demonstrations, etc.
Smart Interactive Whiteboard can help us work and teach more efficiently.Companies,schools,universities,exhibition centers,business centers,Smart board for school,Interactive board for classroom,Smart version,Smart board interactive,Smart board for home can be used everywhere.
Smart board for school,Interactive board for classroom,Smart version,Smart board interactive,Smart board for home
Jumei Video(Shenzhen)Co.,Ltd , https://www.jmsxdisplay.com